Injection
Module 1: Injection Attacks
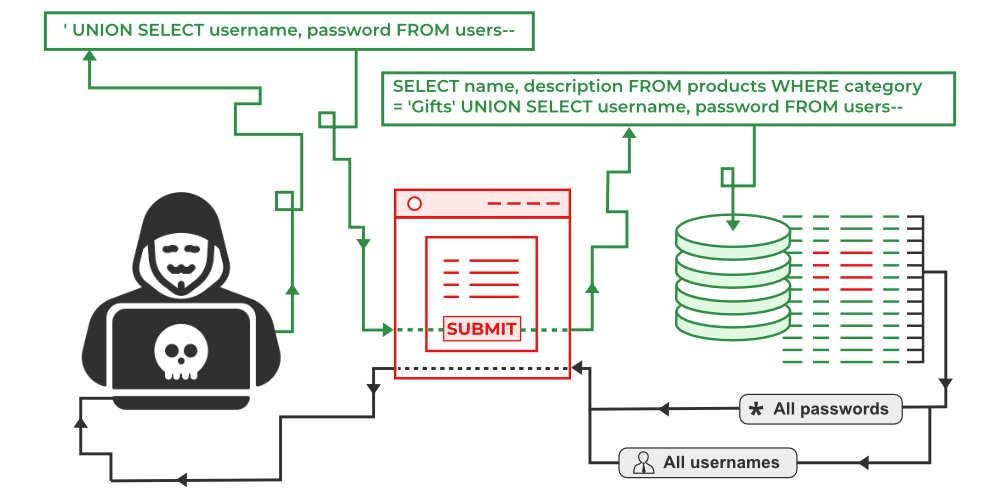
Injection vulnerabilities currently rank third for most common cyber attacks (OWASP Top 10 list) , appearing in 94% of tested applications.
This course will provide an in depth understanding of Injection attacks by differentiating the different types of attacks, demonstrating how an attack might happen, along with some tools to help developers protect against injection attacks.
Retake this course?
Retaking this course from the beginning will reset all of your tracked progress.